Here I will describe how we can transfer the VPN client (Cisco AnyConnect) installed in the "Windows 10" system to the NEWIFI-D2 router with the padavan firmware installed using the OpenConnect applications.
In my case, authorization to the VPN network in the Cisco AnyConnect application, in addition to entering the password, also needs a certificate that is saved on our computer. First, we open the AnyConnect configuration file:
C: \ Users \% USERNAME% \ AppData \ Local \ Cisco \ Cisco AnyConnect Secure Mobility Client \ preferences.xml
In this file, the tag "ClientCertificateThumbprint" is the ID that identifies the certificate used for authorization.
We open the certificate management tool - "certlm.msc" and then in the "Personal -> Certificates" folder we are looking for a certificate with the same identifier in the "Thumbprint" item
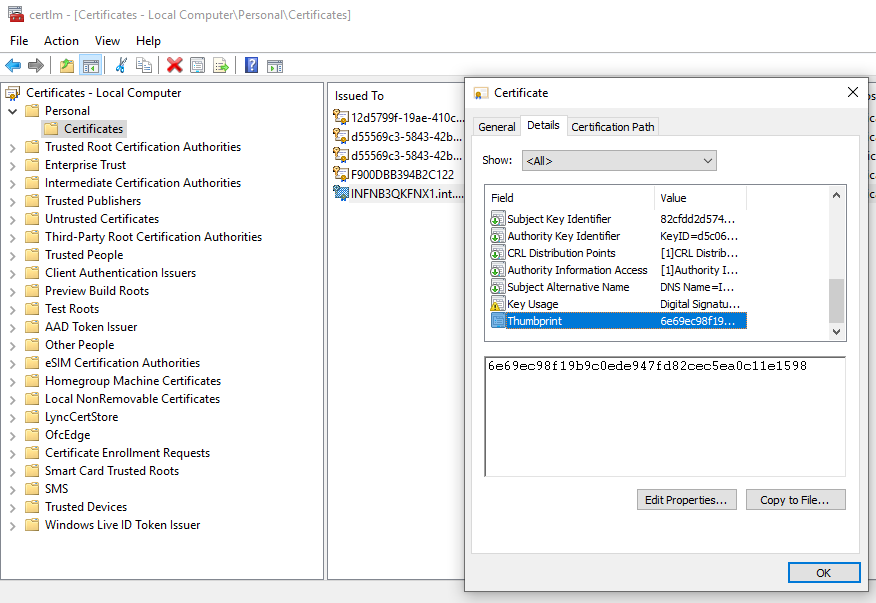
We have to save this certificate together with the private key - here we have the first problem because the private key export has been blocked.
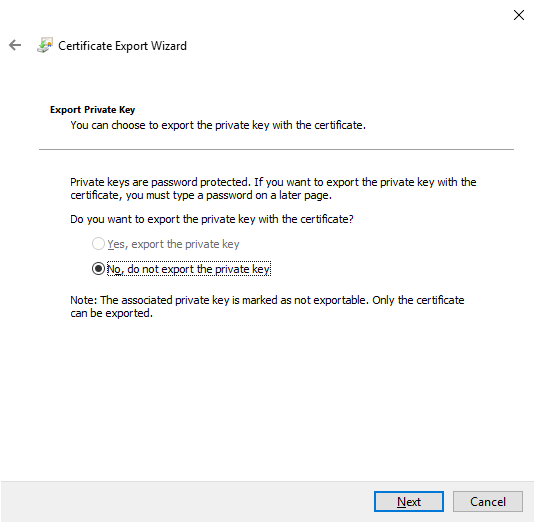
This is where a project called Jailbreak comes in handy , which allows you to export a private key. We edit the file named "jbcert64.bat" as follows:
@ jailbreak64.exe% WINDIR% \ system32 \ mmc.exe% WINDIR% \ system32 \ certlm.msc -64
Now we can run the script and save the certificate together with the private key. The certificate is saved in the " Personal Information Exchange - PKCS # 12 (.PFX) " format , which must then be converted to a form understandable for the OpenConnect application using the command:
openssl pkcs12 -in certificate.pfx -out certificate.cer -nodes
The OpenConnect application is available on the padavan firmware thanks to the Entware repository . After installing, using the "opkg" command, we run OpenConnect with the following parameters:
/ bin / echo "PASSWORD" | / opt / sbin / openconnect VPN_SERVER -i tun2 -c CERTIFICATE.cer -u USER --passwd-on-stdin -l -b --servercert FINGERPRINT
where we change particular variables like password, vpn_server, user, etc. We can add this command to "autostart" scripts in the system. We also need to allow our local LAN to access the remote VPN via iptables:
/ bin / iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o tun2 -j MASQUERADE
That's it - from now on we have access to a remote VPN network without the need to log in to the Cisco AnyConnect application every time ;-)
I noticed that the VPN server will try to disconnect us after a certain timeout. We can protect ourselves from this by using a simple script that will run in the background on the router.
while [1]; to curl WEBSERVER; sleep 60; done
This script, running in a loop, makes a query to the web server on the remote network and then waits one minute for the next call. In this way, our connection is constantly maintained and there is no "timeout" on the server side.
I must admit that my main motivation for this configuration was the access to the network in which the domain controller operates - Active Directory. As you know, the AD service is based entirely on DNS, so we must be able to query the remote DNS server from our local LAN network where the AD service is running.
We need to configure our local DNS, in this case Dnsmasq to forward "domain" queries to a specific server using such an entry in the "dnsmasq.servers" file
server = / domain / server_address_DNS_VPN
thus, specific queries to the domain controller service will be properly resolved. We can now check if our computer is properly communicating with the domain controller.
nltest / sc_query: domain
Flags: 30 HAS_IP HAS_TIMESERV
Trusted DC Name \ domain
Trusted DC Connection Status Status = 0 0x0 NERR_Success
The command completed successfully
