LivePerson is a popular platform that offers the possibility of integrating live chat functions on your website. It also offers the possibility of creating something called 'AI-powered chatbots', i.e. bots that, when properly programmed / set, will be able to service customers themselves and answer frequently asked questions - all of this can be built using a tool called "Conversation Builder "and is available from a browser on LivePerson's servers.
Quite an interesting solution that I focused on is the possibility of programming your bot using JavaScript using special functions. Below is an example of displaying what the user wrote in the chat window to the bot.
var response = botContext.getCurrentUserMessage();
botContext.sendImmediateReply('I think you said, ' + response);We can also execute any JavaScript code like loops, conditional statements and then pass it directly to the bot and display it to the user.
The freedom to execute JavaScript code in this context particularly interested me in terms of the security of such solutions, because it was executed on the server side, which theoretically posed a potential threat.
After executing a special piece of code, I found it worth a closer look.
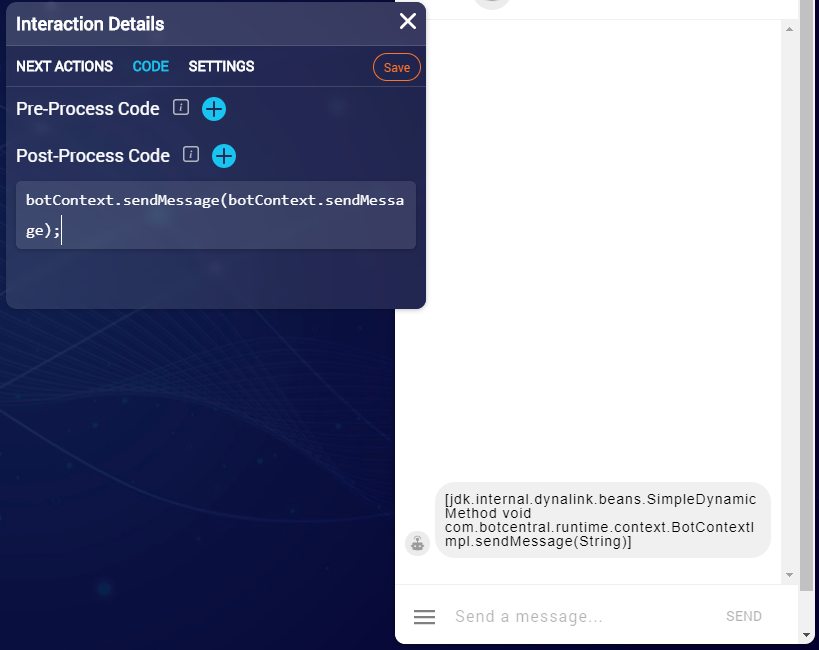
Here we see that the JavaScript code is actually executed by the Java machine and then the result is returned - which is a Java sandbox for JavaScript.
At this point, I started to search the internet to see if it is possible to "jump out" or bypass such a security to execute Java code, so that I would be able to execute commands on the host system - as it turns out , it was possible and it was not particularly complicated ;-)
this.engine.factory.scriptEngine.eval('java.lang.Runtime.getRuntime().exec("whatever")')Nashorn Sandbox was used here, which until version 0.1.19 had a bug that allowed this type of attack - sandbox escape.
May 13, 2020 - application to LivePerson.
5/14/2020 - Thanks for reporting a bug.
